
Continuous Threat Exposure Management (CTEM) is more than just a trendy term, it represents a major shift in how organizations handle security.
CTEM is a new approach that combines proactive security solutions to provide a complete view of vulnerabilities, visibility, and how to coordinate responses.
Gartner highlights that a Continuous Threat Exposure Management (CTEM) program is essential for identifying and prioritizing the biggest threats to a business.
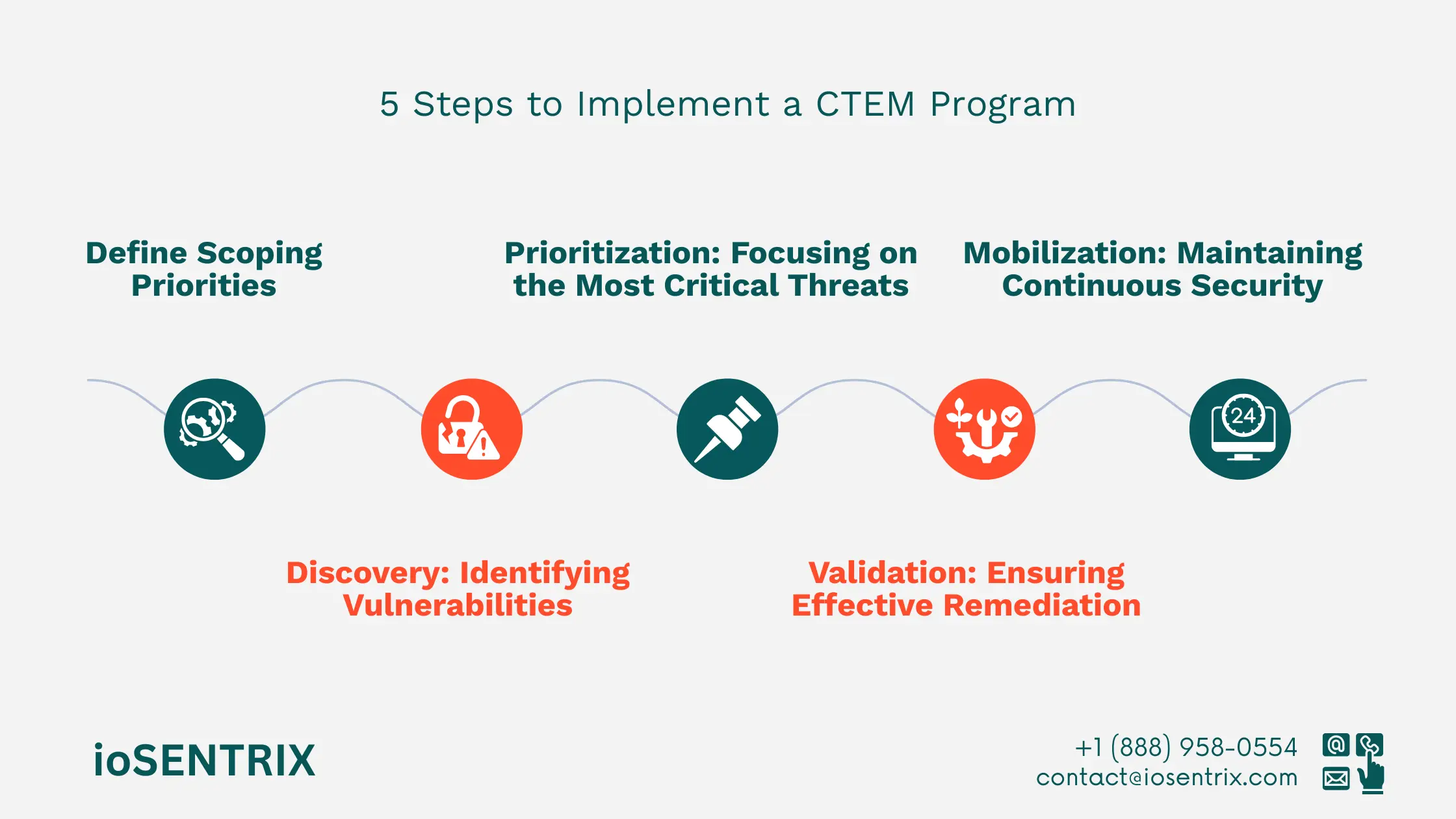
Developing such a program involves a five-step process that helps organizations regularly evaluate how accessible, visible, and vulnerable their digital environments are.
Unlike traditional Risk-Based Vulnerability Management (RBVM), which mainly detects vulnerabilities, CTEM also emphasizes governance, improving processes, and making long-term changes to reduce cyber risk effectively. This makes CTEM a strong foundation for continuous cyber threat exposure management strategies.
Begin by clearly defining your goals and aligning them with business priorities. In this stage, identify critical assets, assess how they could be impacted, and encourage collaboration within your organization.
This ensures a clear and focused plan for threat exposure management that aligns with business needs.
Use both penetration testing and an attack surface management tool to uncover all assets, including hidden ones.
Penetration testing provides a snapshot of how vulnerable critical assets are at a specific point in time, helping prioritize the next steps in continuous threat exposure management.
An attack surface management solution offers continuous visibility of all known and unknown assets. It enhances understanding of overall risks and supports effective continuous exposure management.
Not all risks can be fixed immediately, so prioritize those that could cause the most harm. Evaluate both the technical severity and business impact.
By doing so, you can address the most critical vulnerabilities first, the ones most likely to be exploited in cyber threat exposure scenarios.
Regularly test and re-test vulnerabilities to confirm if they can be exploited. This ensures that mitigation measures are effective. Methods like breach and attack simulations, red team exercises, and penetration testing validate the strength of your continuous threat exposure management program.
Resolve high-risk vulnerabilities and monitor progress continuously. Develop ongoing plans to manage threats, provide team training, and ensure alignment with updated security practices. This stage ensures your organization matures in its continuous cyber threat exposure management efforts.
Gartner predicts that by 2026, organizations that invest in a CTEM program will experience about two-thirds fewer breaches.
Shifting to a proactive, continuous exposure management model helps security teams allocate resources effectively and reduce wasted effort.
Cyber threats evolve quickly, and continuous threat exposure management allows teams to keep pace. By identifying and addressing vulnerabilities early, security teams can reduce risks and respond faster to potential threats.
Beyond short-term fixes, CTEM emphasizes governance and ongoing improvement. This builds resilience by preventing recurring issues and strengthening security processes for sustainable continuous threat exposure reduction.
ioSENTRIX integrates CTEM principles into its cybersecurity platform, aligning with scoping, discovery, prioritization, validation, and mobilization.
The platform includes Attack Surface Management, Penetration Testing as a Service, and Breach and Attack Simulation, all designed to support your continuous threat exposure management goals.
ioSENTRIX PTaaS delivers over 50 types of penetration tests to uncover vulnerabilities, exposures, and misconfigurations.
The platform offers real-time results and expert recommendations to help prioritize risks and streamline continuous exposure management. PTaaS also retests, fixes and monitors new threats, ensuring alignment with CTEM.
ioSENTRIX’s ASM approach combines External Attack Surface Management (EASM) and Cyber Asset Attack Surface Management (CAASM).
Through services such as Full Stack Security Assessments, Secure SDLC/DevSecOps, and advanced penetration testing, it ensures ongoing cyber threat exposure management.
This provides visibility into the digital attack surface, contextual insights, and continuous assessments, enabling security teams to focus on the most critical exposures first.
ioSENTRIX BAS supports CTEM implementation by simulating real-world attacks against specific threat actors and malware techniques.
Through red team assessments and advanced testing, organizations can validate defenses, identify weaknesses, and enhance mobilization strategies.
Findings are mapped to frameworks like MITRE ATT&CK, with detailed remediation guidance to help close gaps and reduce continuous cyber threat exposure.
Continuous Threat Exposure Management (CTEM) goes beyond traditional vulnerability management by focusing on ongoing assessment, governance, and long-term improvements. It enables organizations to stay ahead of emerging threats, optimize resources, and build resilience.
Solutions like ioSENTRIX empower businesses to implement CTEM effectively by providing integrated services that improve visibility, validate defenses, and lower long-term risks in today’s evolving threat landscape.