
As businesses shift from traditional cloud setups to decentralized and hybrid environments, the application security landscape is evolving rapidly.
Modern architectures now span smart contracts, off-chain compute, distributed storage, multi-cloud services, and API-driven integrations.
Securing this expanded ecosystem requires more than legacy application security, it demands deep understanding of Web3, cloud-native infrastructure, identity models, and cross-environment trust.
This article explores how decentralized systems differ from cloud applications, the unique risks emerging across both, and how organizations can build secure, resilient applications from code to cloud with ioSENTRIX guiding the entire journey.
A decentralized application (dApp) relies on blockchain networks and distributed infrastructure where logic, data, and identity are not controlled by a central authority.
Instead, users authenticate through cryptographic signatures (e.g., Sign-In With Ethereum), transactions are validated on-chain, and application logic executes through smart contracts.
A modern decentralized ecosystem typically includes:
Common Problems Developers Face
ioSENTRIX Solution
ioSENTRIX provides end-to-end dApp security smart contract audits, SIWE-based auth validation, node and API pentesting, economic attack modeling, cloud/Web3 trust architecture, and full threat modeling across code and infrastructure.
Cloud-native applications rely on centralized compute models such as AWS, Azure, or GCP with enterprise IAM, CI/CD pipelines, containerized workloads, and API-driven services.
While more traditional, cloud security remains increasingly complex as environments scale across microservices, Kubernetes clusters, identity providers, and serverless layers.
Key components of cloud application security include:
Common Problems Developers Face
ioSENTRIX Solution
ioSENTRIX strengthens cloud environments through cloud pentesting, API assessment, CI/CD security evaluations, Kubernetes/containers audits, compliance mapping, and continuous monitoring via PTaaS.
Cloud systems rely on centralized governance and identity, while decentralized apps depend on cryptographic identity, distributed consensus, and transparent code execution.
Below is a detailed comparison:
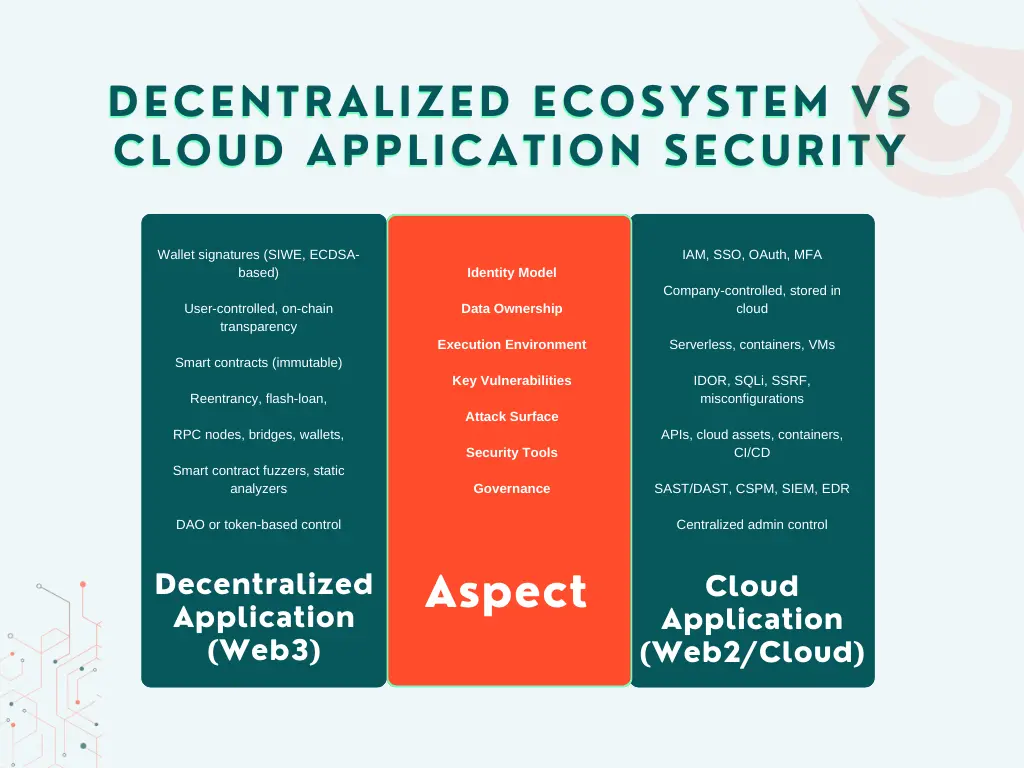
The right architecture depends on your product, user needs, regulatory constraints, and scalability goals.
ioSENTRIX specializes in hybrid architecture security, combining:
This provides end-to-end visibility across both centralized and decentralized components, ensuring your full stack is hardened against real threats.
As applications evolve beyond centralized cloud and into decentralized ecosystems, security must advance with equal sophistication.
Organizations building modern digital products must adopt a unified, hybrid approach, one that secures code, cloud, and on-chain components with equal rigor.
ioSENTRIX delivers this unified security model. With certified experts, advanced PTaaS capabilities, and deep experience in Web3, cloud, and hybrid architectures.
We provide comprehensive protection from code to cloud to chain ensuring resilience, trust, and compliance for the next decade of application development.
dApps are applications that run on blockchain networks, using smart contracts and wallet-based authentication instead of centralized servers or traditional identity systems.
Ethereum is the most widely used platform for building dApps, followed by Solana, Polygon, Avalanche, and Binance Smart Chain.
dApps rely on smart contracts (Solidity, Rust), RPC nodes, distributed storage (IPFS), wallets, oracles, and frontends connecting through Web3 libraries.
They represent a major evolution in digital ownership and trust, especially for finance, gaming, identity, and marketplaces. Most enterprises will adopt hybrid models blending cloud and blockchain.
Solidity, Rust, JavaScript/TypeScript, Python, Go, and frameworks such as Hardhat, Foundry, Kubernetes, Terraform, and serverless technologies.